Information Security Policy
When it comes to keeping information assets secure organizations can rely on the ISOIEC 27000 family. Our community of professionals is committed to lifetime learning career progression and sharing expertise for the benefit of individuals and organizations around the globe.
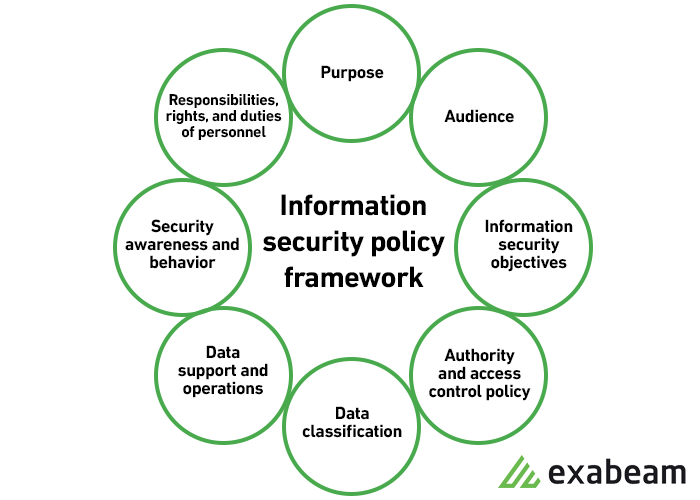
Information Security Policy Everything You Should Know Exabeam

Maintain The Effectiveness Of Your Organization S Information Security Policies Bizzsecure

Pdf The Enterprise Information Security Policy As A Strategic Business Policy Within The Corporate Strategic Plan Semantic Scholar
Since the Center for Security Policys founding in 1988 we have challenged establishment orthodoxy and refused to sacrifice principles for expedience in Washington.

Information security policy. The standard insurance amount is 250000 per depositor per insured bank for each account ownership category. We protect the confidentiality integrity and availability of Penn States information from unauthorized use access disclosure modification damage or loss. Discrimination Harassment Retaliation Sexual Misconduct Dating and Domestic Violence and Stalking against Employees and Third Parties Student Conduct Procedures CSU General Education Breadth Requirements Credit for Prior Learning Policy CSU Contracts and Procurement Policy.
Stack Exchange network consists of 178 QA communities including Stack Overflow the largest most trusted online community for developers to learn share their knowledge and build their careers. For 50 years and counting ISACA has been helping information systems governance control risk security auditassurance and business and cybersecurity professionals and enterprises succeed. This section of the SSA Program Policy Information Site contains the public version of the Program Operations Manual System POMS.
Mission operators use HSIN to access Homeland Security data send requests securely between agencies manage. Our community of professionals is committed to lifetime learning career progression and sharing expertise for the benefit of individuals and organizations around the globe. For 50 years and counting ISACA has been helping information systems governance control risk security auditassurance and business and cybersecurity professionals and enterprises succeed.
Protective Security Policy Framework. First Security Bank - Sleepy Eye First Security Bank - West First Security Bank - Canby and First Security Bank - Mapleton are separate banks with their own charters. Our mission is to secure Americas founding principles and freedom through forthright national security analysis and policy solutions.
The RSA- and DSA-based ciphers are specific to the signing algorithm used to create SSL certificate. The Homeland Security Information Network HSIN is the Department of Homeland Securitys official system for trusted sharing of Sensitive But Unclassified information between federal state local territorial tribal international and private sector partners. The Center for Education and Research in Information Assurance and Security CERIAS is currently viewed as one of the worlds leading centers for research and education in areas of information security that are crucial to the protection of critical computing and communication infrastructure.
All DHS information technology systems technologies rulemakings programs pilot projects information collections information sharing activities or forms that collect personally identifiable information or have a privacy impact are subject to the oversight of the Chief. The safety and health of our community is always the highest priority and we will continue to monitor developments right up to the scheduled event. DoD Instruction 520048 Controlled Unclassified Information CUI DoD Instruction 130017 Religious Liberty in the Military Services.
In keeping with the strong University tradition of service the Centers research teaching and events address digital technologies as they interact with society. The gov means its official. The higher the level the greater the required protection.
The Center for Information Technology Policy CITP is a nexus of expertise in technology engineering public policy and the social sciences. Federal government websites often end in gov or mil. The Office of Information Security OIS establishes implements and maintains a University-wide security program.
The primary use of the HHS ID number you provide to enter the training system is to allow the tracking system to record trainings and associated agreements you take to be eligible to receive and maintain an Active Directory network account andor be granted other authorized access such as privileged and remote access. DoD In struction 613003 Volume 2 Medical Standards for Military Service Retention. Safely albeit with limited attendance.
ISOIEC 27001 is widely known providing requirements for an information security management system though there are more than a dozen standards in the ISOIEC 27000 family. The Information Security Policy consists of three elements. The same-origin policy is a critical security mechanism that restricts how a document or script loaded by one origin can interact with a resource from another origin.
As part of our continuing commitment to the security of electronic content as well as the electronic transmission of information the Commonwealth has taken steps to safeguard the submission of information by implementing detailed technology and. SANS has developed a set of information security policy templates. The POMS is a primary source of information used by Social Security employees to process claims for Social Security benefits.
Before sharing sensitive information make sure youre on a federal government site. DoD Instruction 101016 Technical Procedures for the Military Personnel Drug Abuse Testing Program. Our work is rooted in the proven strategy of Peace Through Strength as applied to the.
DHS accomplishes its mission while embedding and enforcing privacy protections and transparency in all DHS activities. Develops security classification policies for classifying declassifying and safeguarding national security information generated in Government and industry. Security Policy Print Close We take our responsibility to safeguard your information very seriously and employ multiple safeguards in order to help insure that your information is protected as it is transmitted from your computer and stored on our computers at Liberty Mutual Insurance.
Based on the information we have heard we believe our October dates October 25-29 will enable us to produce The SUMMIT. Evaluates the effectiveness of the security classification programs established by Government and industry to protect information vital to our national security interests. Collection of this information is authorized under 5 CFR 930301.
Policy Statements Requirements How Tos Choose a Security Control level below to view associated Requirements based on the higher of the two data risk level or system risk level. These are free to use and fully customizable to your companys IT security practices. For more information see Update the SSL negotiation configuration.
For example it prevents a malicious website on the Internet from running JS in a browser to read data from a third-party webmail service which. It helps isolate potentially malicious documents reducing possible attack vectors. Alternatively you can create a custom security policy.
QA for information security professionals. Our list includes policy templates for acceptable use policy data breach response policy password protection policy and more. Home Security Policy.
The Protective Security Policy Framework PSPF assists Australian Government entities to protect their people information and. Who We Are.
1

Having A Good Understanding Of The Information Security Policies And Procedures Will Not Skillset

Cimtas Information Security Policy

What Is An Information Security Policy Upguard

Employees Adherence To Information Security Policies An Exploratory Field Study Sciencedirect

Security Policy Fuji Electric Hangzhou Software Co Ltd

What Is Information Security Types Of Security Policies Infosavvy Security And It Management Training

Information Security Policy What Should It Look Like